Types of Wireless Network Attacks & How to Defend them
In today’s world, everything is connected to the internet. From a small shop to a large business and different sectors and industries can not run without the network connection. First, it was done with the help of a wired network.
But managing the wired network is a very difficult thing and the second problem with the wired network is the cluster of wired. To get rid of this a new form of the network came into existence known as a wireless network.
The wireless network is now using all over the world. With the help of this daily, a large number of transactions are carried out across the network. Whether you are at home connected to a wifi or at a shopping center paying the bills wirelessly.
It is a convenient and most affordable network method compared to the wired network. The network is cluster-free and even faster than the wired one. But on the other hand, it also has some drawbacks which we can’t ignore.

And most of the people even don’t know about this drawback. But if you use a wireless network then you must be aware of these types of wireless network attacks.
What is a Wireless Network Attacks?
Wireless Network Attacks is a type of attack that targets the wireless users to capture and intrude the information transmitted over the network. In today’s world, everything is connected online and most of the world’s population uses mobile devices to communicate with various facilities wirelessly.
The attackers basically work as a middle man to capture the data transmitted over the network and then send it to the attacker’s server.
There are different types of wireless network attacks based on their level of security. According to the paper published in the research gate, the wireless network is of three types – Level I Security, Level II Security, and Level III Security.
- Level I Security (WEP) – This level of security is based on the algorithm called Wired Equivalent Privacy (WEP). The WEP algorithm is designed in such a way so that it can eliminate most of the security threats over the network by encrypting the data transmitted over the network. Only the receipt with the correct WEP address can decode the data and use it.
- Level II Security (WPA) – This level of security is based on the algorithm WiFi Protected Access (WPA). It is a mid-range of the security but more powerful than the basic level I Security. This type of security applies to the stronger network access and provides an extra layer of security along with the speed.
- Level III Security (WPA2) – This is the most advanced level of security which is mostly used on all the type of network device such as routers. Launched in 2004 this is the highest level of security till data and it is also known as 802.1 li.
Based on the level of security I am going to share the top 8 types of wireless network attacks of 2021 that had a very high impact on the system.
You should Also Read | 10 Best Ethical Hacking Tools in 2020 For Windows, Linux & Mac OS
1. Rouge Access Point
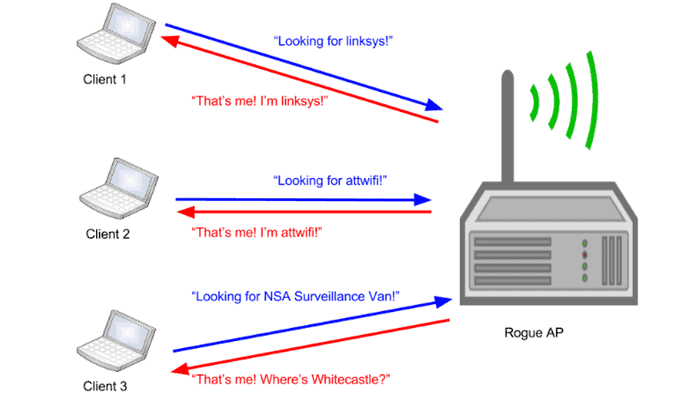
When an unauthorized access point appeared in the network it is referred to as a rouge network. This type of access point is implant by the malicious attackers in order to create a fake access point to lure the network employees who are not much aware of the access points.
This type of wireless network attack allows the attacker to run various types of vulnerability scanners to find the system’s weakness. And once the weakness found the attacker can do various types of attacks including ARP poisoning, packet captures, and Denial of Service attacks.
2. Packet Sniffing
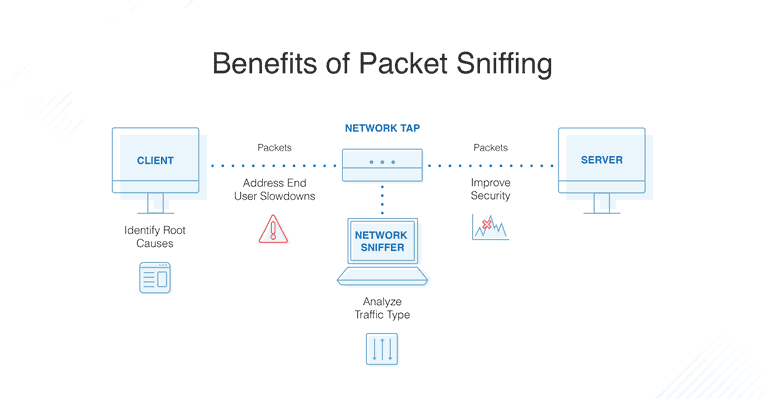
When the information is transferred or received over the network it is called packets. Since we are using the wireless network therefore the packet is in the air and easy to capture using many tools such as Wireshark.
Quite a lot of traffic (FTP, HTTP, SNMP, etc.) is sent in plain text format which means it is easy to read by anyone on the network. The attackers use different tools to capture this sensitive data which can lead to stolen the password.
The encrypted data is also transferred over the air but they are much safer as compared to plain text. Because the attackers still need to decrypt the data after capture that which is quite difficult based on the encryption method.
3. War Driving
Wardriving is a technique in which one searches for the access point nearby or where they are. With the help of free wifi connection, they can drive over a large area to lookout the access point which they could target in a short period of time.
Some companies that own multiple floors or very far from public places think that nobody going to attack them and their network is safe but some attackers can also use drones to find all the access points in a short time at these locations.
4. Jamming
As the name states, this means jam the network with some kind of interface. This interface could be a nearby Bluetooth headset, a micro oven, or a cordless phone. The main purpose of this type of wireless network attack is to jam the network so that even a legit transmission also stops.
There is a number of ways to jam the network. One of the popular methods is to flooding the AP with deauthentication frames. This will overwhelms the network and continuously stop the legit transmission to be done.
In this types of network attacks the attacker got nothing but can slow down your transmission.
5. Password Theft
When going through a website you might see an SSL or a padlock symbol on the browser that means your data transmission is safe and encrypted. Imagines that there is no SSL or TLS then whatever the data you will send like password, credit card detail would be in a plain text format and an attacker can easily grab them just like a middle man.
Not only the attacker can capture this data but also can modify the content of the transmission. For example, it can modify the email content that you are sending to a user.
If you are interested in becoming an ethical hacker then you should read these 15 best ethical hacking e-books and learn more about these types of attacks.
6. Middle Man Attack
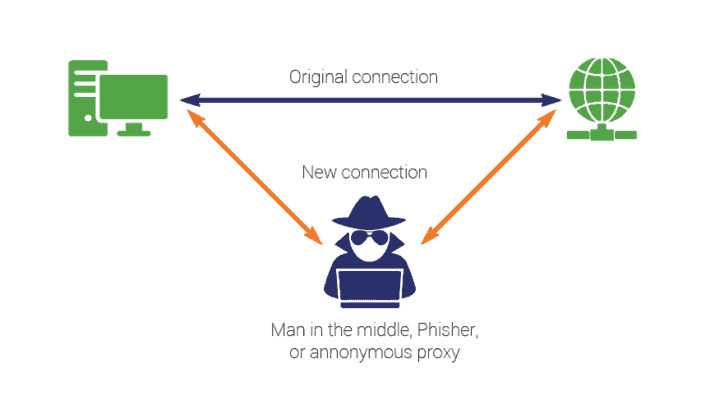
Also known as the man in the middle network. It can trick the communicating device and send the data transmission to their network. It is just like a packet sniffing on the air. Similarly in this, the original data are theft to the attacker’s server.
The attackers can also inject the malware in the data transmitted so that it can grab more information for the receiving end too. Mostly these types of attacks are done in email and messages. So always use a powerful and safe email client like Gmail which scans the content before you open them.
7. Mac Spoofing
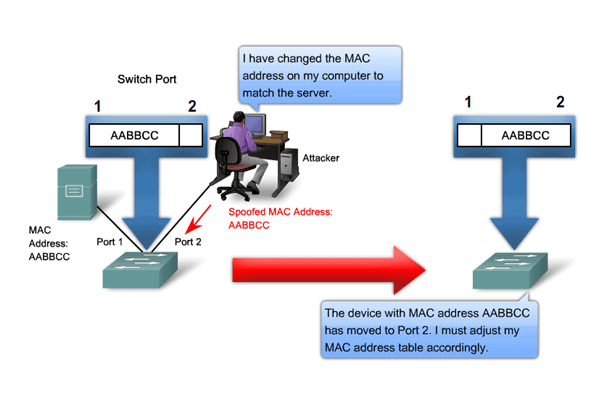
Media Access Control (Mac) is assigned to reach and every network device so that one can identify the device connected to the system and can communicate with them. But some users can change the mac address of the device to the device already registered to the system.
By doing so that can easily connect to the system without any issue. Some users also use the Mac filtering feature but this could also mislead by Mac spoofing which is very common nowadays. But still, it is effective.
8. Social Engineering
This is the most common network attack use to grab the social media account of the users. Unlike all the other wireless network attacks this social engineering does not require any type of script or tool. With the help of social engineering, one can easily clone a website and grab the user credential detail.
Kali Linux is one of the best tools to learn how social engineering works. With the help of Kali Linux, you can do social engineering in just 1 minute. Just enter the website address and it will create the same website in a few seconds.
Then this clone site is used to capture the user credential detail or credit card number of a bank customer. All the information which customers provide here will go to the attacker’s server and you are in attack.
How to Prevent Wireless Network Attacks?
Not all the type of wireless network attacks can be prevented but some of them can. So ensure you must go through this process to secure your wireless network. Also, read Best Method to Hack WiFi Password on Laptop so that you can get an actual idea of how the hack works.
1. Don’t get Router from ISP
This is the most common mistake that every new network user do. This type of routers are manufactured in a bulk from countries like China and they have their own customized firmware over which your ISP does not have any control.
This means if there is a security issue with the routers then it would take a long time to patch. Sometime you might also not get security patches over a period of time which create a lot of security issue for the network.
2. Update Router Firmware
Try to make a habit to frequently check for the firmware update for the router. Even when you buy the router you should first check the firmware update after setting up the system. The firmware update could improve your router performance and also improve the security of the network.
3. Change Default Credentials
I have seen most of the router users never change their default login credential details. Only they change the WiFi access point name and password. But one should also change the default router username and password because they are very common.
Once the attacker got connected to your network he can easily log in to your network control panel when you have the default username and password. Creating a strong password is a great choice and also if you forget the credentials it is easy to recover them.
4. Secure your WiFi Network
While setting up the login credential create a password that is hard to guess and also change the username. Never keeps your network as open for all always ensure a security protocol such as WPA2 which is very hard to crack.
If you have guest users you can enable the guest feature. And always ensure rate-limiting in the route configuration so that one cannot send too many authentication packets. For Mac spoofing enable the Mac filtering option that will not allow any intruder in the system.



