What is DNS Attacks & how to defend them in 2020?
DNS Attack is an exploit in which hackers took the advantages of weakness and vulnerability of the domain name server.
In today’s life, everything is connected to the Internet, including your household activities or business setup. Not every device or a system is secured fully but sometimes they left some weakness on the system known as vulnerabilities.
Attackers took advantage of these vulnerabilities to exploit in the system and hijack your data by many methods.
Every website you visit on the internet has its DNS server which resolves to an IP address to provide contents and data to you. In the middle of this hackers took advantage of the weakness of the system and perform hacks.

In this post, I am going to tell you about the DNS attack and its types. Along with this, I will provide you certain tips to defend them.
What is DNS Attack?
DNS attack happens when an attacker took the advantages of weakness hidden in the domain name system.
Hackers took advantage of these vulnerabilities to perform the DNS attack and hijack user’s data and contents.
Yes, it is a big headache for many big tech firms also. In recent past years, many top tech companies face this attack and got victims of that for a long time.
Know how to hack a wifi network in 5 minutes with your android phone.
In order to understand a DNS attack you first have to understand how a DNS works.
DNS (Domain Name System) is a function that converts your web address into an IP address to provide you content from the server.
How DNS Works?
When a user types a web address in the browser a program available in the operating system knowns a DNS resolver look fo the IP address of that particular web address.
For example, let us take google.com
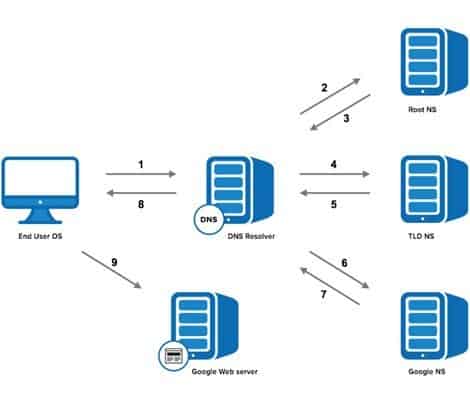
So when a user types google.com in the browser, the DNS resolver looks for the IP address in its local cache.
If it found IP address in the local cache then it will return the query to the browser to show the requested content stored in this IP address.
If DNS Resolver was unable to find an IP address in its local cache then it will request another DNS Server for IP. DNS servers are work in a loop so when a server was unable to find IP it will look for another server.
Once the DNS Server locates its IP address it will submit this IP to the requested DNS Resolver and the content will be shown to the user.
DSn resolver also stores this IP address in its cache for future use.
Although the Domain Name System is quite powerful yet it is less focused on the security and this is the reason why all these DNS attacks happen.
Types of DNS Attacks
There are many types of DNS attack are done by hackers based on there security and demands.
When one attack fails on the system they try other attacks, while some of these attacks is very popular and listed below.
Zero-Day Attack
In this type of attack, the attacker exploits a formerly unknown vulnerability in the DNS server software or protocol stack.
Currently, there are no patches have been released to fix these vulnerabilities in the vendor system.
DNS Spoofing
DNS Spoofing or DNS Cache Poisoning is a very serious issue nowadays. In this, the hackers replace the authorized IP address with the bogus IP address in the server cache.
It typically redirects all the traffic to a malfunctioned website to collect all the crucial and confidential detail of the users.
With the help of these, they can also get the banking information like your credit card no and net banking passwords.
This is one of the most popular techniques acquired by the attacker to steal the information.
Users even don’t realize that they are being targeted by the attackers to steal their information. All this information is sent to a phishing website and stored in the attacker’s server.
The best method to prevent DNS cache positioning is to clear the DNS cache from time to time.
Fast Flux DNS
The attacker swaps DNS records in and out with extreme frequency in order to redirect DNS requests and avoid detection.
DNS Amplification Attack
DNS amplification is a distributed Denial of Service(DDoS) attack in which the attackers target the public domain system and turns the small queries in larger payloads.
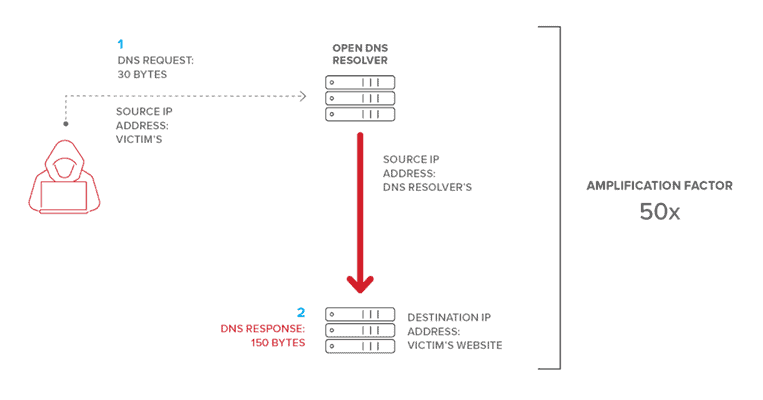
DNS Amplification attack can bring down even the largest infrastructure in a couple of minutes.
In this attack, the attacker makes the uses of infected websites and IoT devices to send a flood of traffic to the original source.
It is just like a traffic jam that stops the original traffic to go on its way.
How to Stop DNS Attacks?
When a DDoS attack hit your server there is no time to think about that all is you have to prepare for that in advance.
So when these attacks take place you have to prepare a plan to stop this attack. You plan should include the following main steps:
- System Checklist: You should prepare a checklist to check all the assets, identification tools, filtering tools and also perform a security checkup on software as well as hardware level.
- A Good Response Team: You should provide responsibility to every key member of the team for an attack, so they could try their best to defend this DDoS attack.
- Notification and escalation procedure: Your team should know whom to contact if the attack is not stopping by theme.
You can also use a content delivery network such as Cloudflare which will help in the protection of your server.
Cloudflare checks all the traffic coming to your server and scan them if there is a possibility of malicious code. It also blocks too many requests from the same IP address which will help in limiting the bandwidth usage.
Conclusion
Most DNS attacks happen when proper security measures are not taken from time to time by the administrator. So always try to take proper security steps and try clearing local cache DNS address regularly.
Read More | Best USB WiFi Adapter Compatible with Kali Linux for Penetration Testing
I hope you have got enough information about the DNS attack and why this happens. If you have any questions about this you can simply ask me in below comment section.



