What is MITM (Man in the Middle) Attack and its Types
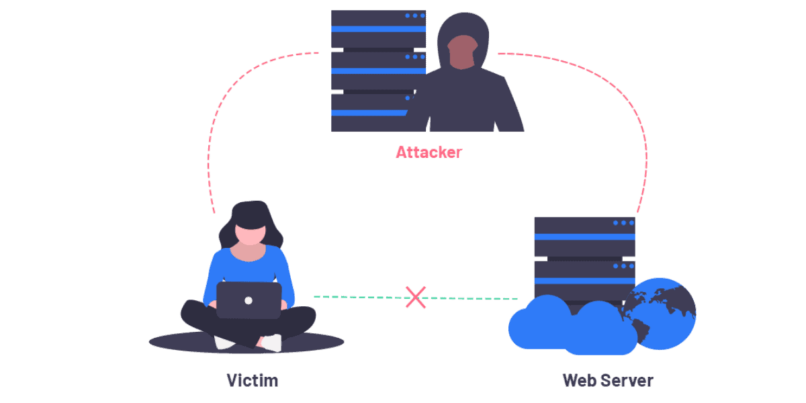
A man in the middle (MITM) attack is a form of cyber attack where a preparator position himself in the middle of a conservation between two parties. Here the parties are a user and a web browser or an application.
The main goal of the man-in-the-middle attack is to steal personal information such as account credentials and credit card details. Organizations like SaaS applications and eCommerce platforms are common targets of man-in-the-middle attacks.
In this type of attack, the attackers intercept the communication, keep an eye on the process and alter the information sent and received between the browser and user.
The information obtained during this attack was used in many ways such as unauthorized transfers and password changes.
A MITM attack is like, a postman opening your mail, writing down your account details and resealing your envelope, and delivering it to your address.
How does Man in Middle Attack work?
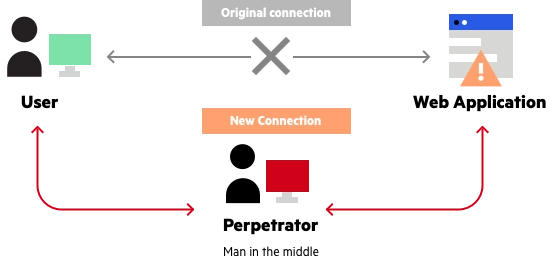
A successful MITM attack has two phases. First is the interception phase where the attacker interprets between two parties. And the decryption phase where the attacker decrypts the captured data over the transmission.
In both phases, the attacker uses different hacking tools to get on the network, capture data, and remain undetected. It is a silent hack where a user doesn’t notice a hack in the system.
1. Interception Phase
In this step, the attacker intercepts the user’s traffic on the network before reaching its intended destination. This can be done by various methods.
One of the famous methods is to create a malicious public WiFi network and lets the victim join it. These networks aren’t password protected and are free to join. The name of these networks is in such a way that it corresponds to the name of the address or a business.
Like a free WiFi network of a coffee shop. And once the victim connects to this network, the attacker gets full visibility of the data over the network.
2. Decryption Phase
In this phase, the traffic intercepted during phase 1 has to be decrypted without altering the user and application.
The attackers basically send a phony certificate to the victim’s browser to make a secure connection. Once the secure connection is made, it holds a digital thumbprint associated with the application.
So when the victim entered the data, the browser sends it to the attacker. Because the attacker is already in the trusted list of the browser.
In this way, an attack holds the victim’s data and now can use this data to perform various illegal activities.
What are Man-in-the-middle Attack types?
Here are some of the common techniques the attacker uses to become a man-in-the-middle.
1. ARP Cache Poisoning
ARP (Address Resolution Protocol) is a low process technique that translates a machine address into the IP address of the network.
This method tricks the computer in such a way that it thinks the attacker’s computer is the network gateway. When you connect to this network, the attacker receives all your traffic passing to a real destination. So you won’t be able to notice any unusual.
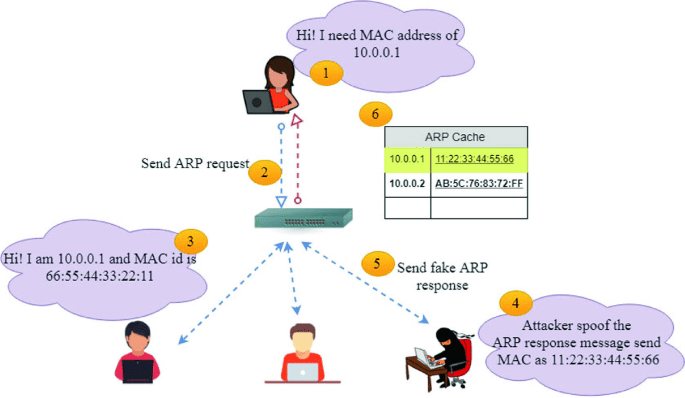
- With this method, the attacker joins your network and runs as a sniffer.
- Then the attacker inspects your network and predicts the number of packets between you and the gateway.
- After this, the attacker sends a spoofed packet with a fake source address to your computer. This makes the ARP sequence fool your computer into thinking the attacker’s computer is the gateway.
- At the same time, the attacker will flood your network with a DoS attack, so you receive fake ARP packets. This all happens even before your gateway responds to your request.
- This makes your computer think, that the attacker’s computer is the real gateway. And make the man-in-the-middle attack successful.
2. HTTPS Spoofing
When you visit a website, you might have seen a green padlock sign in front of the website address in the UR bar. This represents that the system is secure using the HTTPS authentication method.
Likewise, the attackers create a legitimate website with a valid certificate but with a different address. The address is a little bit different so you can not notice it even after looking for hours. Because the website address uses a different Unicode character.
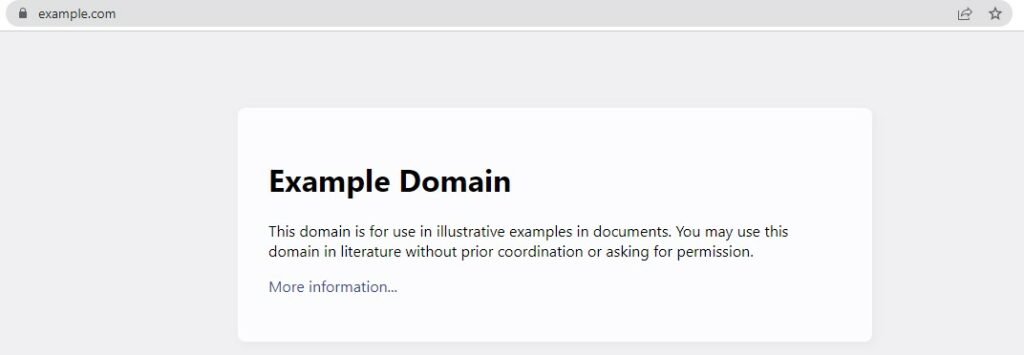
For example, the website example.com will look like https://example.com, but this is not the same. Here the attacker uses a different Unicode character value for ‘a’ in Cyrillic that looks similar to an Arabic “a”.
- The attacker uses the phishing technique to fall you into the trap.
- Once you connected to the fake website, your browser will download a fake CA certificate.
- This certificate is then stored in your browser’s trusted store.
- Now the attacker can listen to all the traffic sent to the fake website address.
3. Session Hijacking
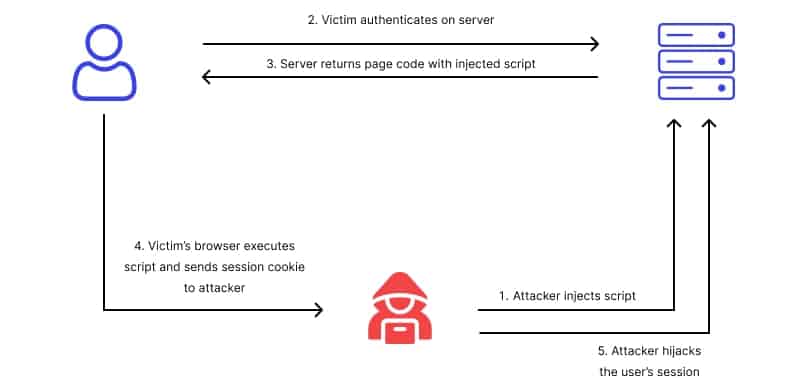
In this type of MitM attack, the attackers rely on your browser’s cookie. When you log in to your bank account the browser saves the session data in form of a cookie. The attackers steal this session cookie to log in to your bank account from a different browser.
Once the attacker has your active session cookie, he can do whatever you can do on the website. He can transfer all your money to an offshore account or can buy anything online from your credit card.
The attacker can use these session cookies until and unless you logged out and changed your password. Once you logged out of the website the browser modifies the cookie and no one can log in with stolen cookies.
4. DNS Cache Poisoning
DNS Cache poisoning happens when an attacker fakes your DNS entry and redirects you to a different website. For you, it might look like a legitime website but it would be an attacker website.
For example, when an attacker fakes your DNS entry, google.com will not be the same as others see. But for you, it will be the attacker’s website that looks like google.com.
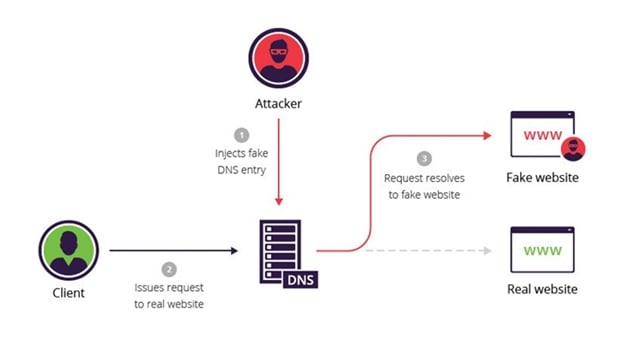
- First, the attacker figures out which DNS resolver you use.
- Then the attacker finds vulnerabilities on your DNS resolver and exploits them.
- The attackers tell your DNS resolver that google.com lives at an IP address that they own.
- So when you visit google.com, the DNS resolver will tell you the IP address of the attacker’s machine.
- In this way, the attacker behaves like a real website and listens to all your traffic. And you won’t realize that someone is intercepting your traffic.
Real-Life Example of MitM Attack
Here is a practical example of the man-in-the-middle attack. In 2020, Microsoft Office 365 has been targeted by a man-in-the-middle (MitM) attack. The attackers bypassed the Microsoft 2FA and hijack the session cookies to log in to Microsoft account.
- First, the attacker sends the fake Microsoft login page to the users where they enter their username and password.
- The webpage forwards the username and password to the attacker’s servers.
- The attacker forwards the login request to Microsoft, so they don’t raise suspicion.
- Microsoft sends a 2FA code to the user via SMS.
- User input the code into the fake webpage.
- The fake webpage forwards the 2FA code to the attacker’s server.
- The attacker steals the session cookie with the help of Evilginx.
- The attacker forwards the two-factor authentication code to Microsoft. Now the attacker can log in to the Microsoft office 365 account as compromised by the user’s session cookie.
How to Detect a Man-in-the-Middle Attack
Although MitM attacks can be difficult to catch an end user or a cyber security expert can spot using irregular network activity. Here are some of the signs that warn you against a MitM attack.
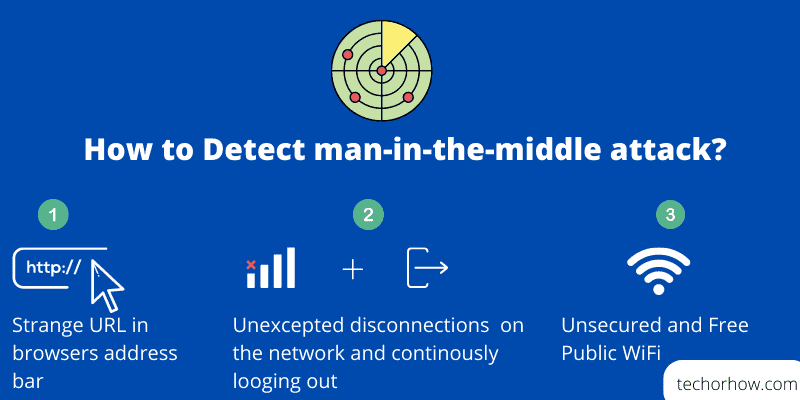
Unexpected disconnection: If you are disconnecting again and again from your network this could be a MitM attack. Because the attackers need to disconnect you so that you can re-enter your username and password.
Check your browser address bar: If you see anything unusual in your browser address bar, double-check it. It could be a DNS hijack or a phishing attack. So look for the website address and also verify that the connection is secure using HTTPS authentication.
For example, the website address is g00gle.com instead of google.com
Never access sensitive information on public WiFi: Be aware while connecting an unsecured or public WiFi. It could be a trap by the attacker. Attackers create public WiFi hotspots so that they trick the victim to connect to a free WiFi and hijack the session cookie.
How to Prevent MitM (Man in the Middle) Attack
To prevent a MitM attack users need to take several actions listed below but are not limited. You should make a hobby of this method to block the attack in the future.
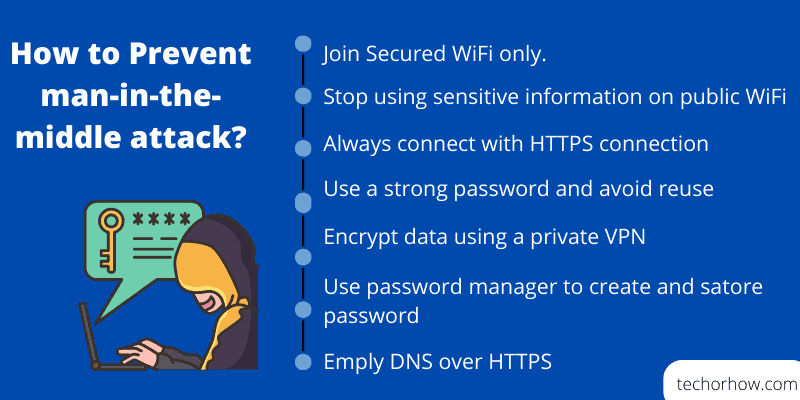
- Avoid using Unsecured and Public WiFi connections.
- Stop using Free WiFi connections in coffee shops and airports.
- Stop accessing sensitive information on public networks and internet cafes.
- Always look for the address bar in the URL.
- Make a hobby to immediately log out of secure accounts like financial accounts.
- Use a VPN to encrypt your traffic between end-points and a VPN server. Encrypted traffic makes it hard for a MitM attack.
- Look for the padlock icon on the browser’s address bar and always connect to an HTTPS connection.
- Use a strong password and prevent the reuse of passwords.
Wrapping Up
Around 35% of attacks that exploit cyber vulnerabilities have been MITM attacks. So consider the seriousness of the attack and take every preventive action to keep your data safe. There are many tools like WiFi pineapple available on the internet that is used to carry out a MitM attack.



